
The following are excerpts from the USPS Office of Inspector General’s “self-initiated audit of selected U.S. Postal Service Active Directory Domains.” The USPS OIG’s objective was to “determine whether selected domains were configured and managed in accordance with policy and industry best practices.
The Postal Service uses Microsoft’s Active Directory (AD) to control access to more than 192,000 information resources on the Postal Service’s information technology (IT) network. AD is a centralized system that allows domain administrators to manage user accounts, computers, policies, and permissions. Users can access systems and services through AD once they authenticate with the proper user name and password. Within AD, domains manage user accounts, including managing groups of users and computers by setting similar policies and providing access to network resources within each domain. Domain controllers are servers running AD services that support a domain.
The USPS OIG conducted its audit work on the =======domains at Postal Service facilities in Merrifield, VA; Norman, OK; and Topeka, KS; and the ========domain in Chantilly, VA.
The USPS OIG ” judgmentally selected and tested 5 of the 168 domains that are not required to follow Sarbanes-Oxley (SOX) and Payment Card Industry Data Security Standards (PCI DSS) based on the highest number of systems they support. We reviewed the =========domains and the =======associated domain controllers.”
Summary of findings
Postal Service management did not appropriately configure and manage the five domains we reviewed on the IT network. We found that up to 40 percent of the security settings we reviewed for each domain did not fully comply with Postal Service security standards. In addition, the Corporate Information Security Office (CISO) did not fully align Postal Service security standards with Microsoft’s best practices and management did not appropriately manage privileged accounts for three of the five domains by having two shared administrator accounts and not privileged accounts. In addition, was not set for three of the five domains and there was no requirement to change administrative account passwords every 30 days for four of the five domains.
These issues occurred because administrators were unaware of applicable Postal Service security standards or did not have access to them and did not have a schedule to review standards periodically to ensure compliance. Management also did not make it a priority to update server security standards to align with best practices and be consistent with Postal Service security standards found in Handbook AS-805. By implementing effective management over AD, organizations can appropriately secure their information resources and reduce the risk of attackers exploiting vulnerable services and settings.
Management of Domain Controllers
Domain administrators did not appropriately configure and manage the domain controllers we reviewed as required by policy. We found that they were not fully compliant with Postal Service security standards related to configuration settings and system service settings.
Configuration settings define the way a computer system or program is set up for a particular use. The non-compliant configuration settings we identified included ============These configuration settings track and log system changes that management can review in the future.
System service settings are programs that load automatically to support the system’s various tasks. These settings can be part of an application’s startup process or an operating system’s startup process. We found that two system service settings were noncompliant: ============service was disabled and ===========service was not installed. These system services are critical for blocking unauthorized network traffic and detecting and removing malware.
Administrators did not configure domain controller security settings appropriately because they were unaware of applicable Postal Service security standards or did not have access to them. In addition, administrators did not have a schedule for periodically reviewing the standards to ensure compliance. Without proper controls and requirements over the domains, the Postal Service is at an increased risk of unauthorized users gaining access to Postal Service resources.
“During our audit, management initiated corrective action by updating the configurations of two of the five domains we reviewed. However, corrective action is needed to address the remaining non-compliant configurations.”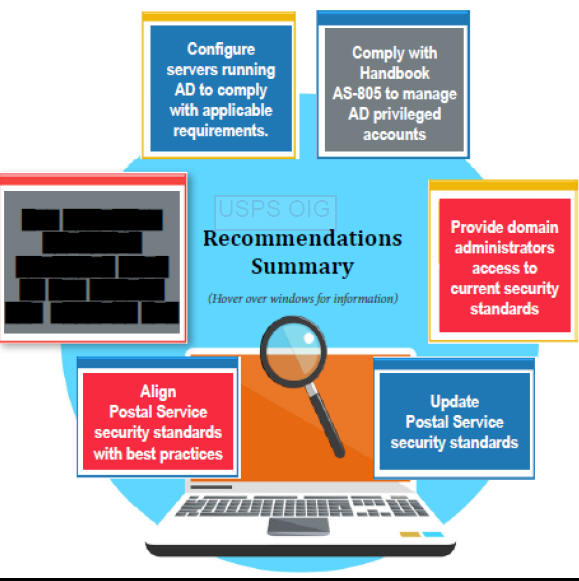
The USPS OIG recommended the acting vice president, Information Technology, coordinate with the vice president, Engineering Systems, and vice president, Network Operations, to:
1. Provide domain administrators access to current security standards.
2. Direct domain administrators to configure servers running Active Directory to meet requirements outlined in applicable Postal Service security standards.
3. Direct domain administrators to comply with Handbook AS-805, Information Security, to manage Active Directory administrative accounts, including =========and are not approved by management, and changing administrative account passwords.
They also recommended the acting chief information security officer and vice president, Digital Solutions:
4. Update current =========server security standards and align them with best practices where appropriate to enhance the overall security of Active Directory
note: ===== stands for redacted text
PO is just a Carnival of Corruption!
This after the infamous hacking incident a little over a year ago? Doesn’t seem like management is following up on its promises to make our information safe and secure to me. But then again, should any of us be surprised?
Time and time again we read reports of malfeasance and incompetence in the management. Granted, there is the same in craft, too, but management seems to be particularly immune to responsibility whereas craft can get removed.
An investigation into the way people are accepted into management overall reveals the inherent cause of so much failure. After three+ decades of working for the USPS, I can assure readers that my observations are accurate, and why management is in a state of disaster.
1) Nepotism I know far too many cases where somebody starts out that just happens to have a parent, uncle, aunt, etc. in a higher level position somewhere in the district. These types are already in before they ever make it past their probation. Whole clans can be found in management, with people getting in without experience, brains or anything besides sharing DNA. Far too often they are mean, show extreme favoritism and create terrible workroom pressure sometimes just for the hell of it. I know one in particular who revels in harassment of those who are disliked, and allowing friends to get away with murder.
2) Sycophants This is the nice way to say snitch and ass kisser. Some can be relatives too, but those not connected by blood can get in if they’re willing to rat out fellow workers, use sex for promotions, and otherwise pal around with supervision and ignore their own craft workers. They’ll do whatever management wants, regardless of whether it violates rules or the JCAM, and try to socialize on and off the clock in return for a shot at the big time.
3) Relentless back stabbing This is after a supervisor/manager wanna be has finally gotten in as a supervisor somewhere who is willing to crush anybody who gets in their way of more money. This is where it can get serious on a national scale. We now see relatives and ass kissers getting into the budgets, safety, overall operations and labor who aren’t any more qualified to be there than any craft employee who wants nothing of the kind, preferring instead to have respect and friends through their career. Many of these types can and do commit terrible mistakes – witness the methane leak deaths for example. Terrible fiscal and operations decisions like shutting down plants and crippling service come from this batch, who are ill trained, self centered and only in it for power and bonuses. This is why we see so much mismanagement because so many are just stupid mean spirited jerks who fancy themselves as big shot executives, when in reality they couldn’t get hired as a real executive because the world knows just how poorly they ruin the USPS.
The solution? Form an independent commission that is not part of the Service to truly oversee and take action on the idiotic behavior management commits. No Board of Governors, OIG, anybody management can bribe or remove. This is a service, not a for profit business, and therefore should be held to external scrutiny and maybe one day remove the incompetents, and replace them with craft people who have proven their intelligence, worth and integrity. Anything less is just pissing into the wind.
Whats stated are true, however, thanks most of management isn’t like you describe. Strange but true how it works for unqualified relatives and friends. Sometimes it hurts later on. The new game in town is people are coming into the service w/o direct processing. Friends of various groups get carte-blanche as a whole, and then inefficiencies occur often. No history of past practices that worked and still will. The best way to describe the present concept is; Go along to get along, and do what you’re told to whomever, regardless of consequences and outcomes.